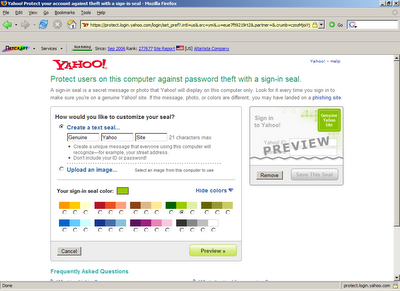
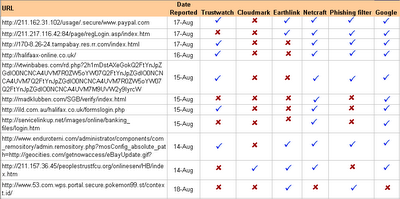
Of late anti-phishing toolbars have been catching my attention. These small utilities can be quite useful in protecting a user from a known Phishing attack. But with so many different anti-phishing toolbar being launched, I thought of evaluating a few. I picked up five popular anti-phishing toolbars for evaluation, namely Anti-phishing Toolbar from Netcraft, Phishing Filter from Microsoft, Scamblocker from Earthlink, Trustwatch from Geotrust and Anti-fraud Toolbar from Cloudmark. These toolbars were evaluated against a set of parameters which is shown in the image below (click on the image to enlarge).

Looking at the evaluation results it is not difficult to interpret which tool has won the first place. Netcraft Anti-phishing toolbar is definitely most impressive and accurate in detecting phishing sites, followed closely by Geotrust’s Trustwatch. I used the following two recently found Phishing URLs to test the toolbar’s accuracy in detecting a known phishing attack,
http://www.yourfreespace.net/users/payal/webscr_cmd=_login-run.html
http://adsl-71-132-90-121.dsl.sntc01.pacbell.net:81/update/
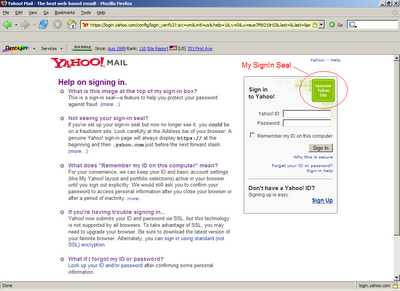
Netcraft alerting mechanism is also good as it displays a message popup as against other tools that rely on a visual icon on the toolbar which users may fail to see if they are not alert. The message popup thrown by Netcraft toolbar is shown below.

Netcraft also provides the most detailed analysis of the website along with a risk rank calculated based on a number of
parameters. The help information available to the users is also quite detailed.
One interesting feature that I found in Trustwatch toolbar is the ‘Personal security ID’ which is aimed to prevent toolbar spoofing by displaying a user selected image or text on the toolbar. The text 'ABHISHEK' in the image below is the 'Personal Security ID' that I set during installation.

Microsoft phishing filter is right now in beta stage and has a lot of catching up to do. Cloudmark and Earthlink failed to detect the phishing sites and their features currently are not very useful. So after all this evaluation my pick is Netcraft Anti-phishing toolbar.