Revisiting 'Referer' Analysis
In the last post on 'referer' analysis, we discussed how ‘referers’ in the web server access logs can be analyzed to detect a Phishing attack. But a manual analysis of web server logs can be difficult and time consuming. However, there a number of tools which can be used for effective and fast analysis of web server logs.
One such versatile tool is SAWMILL . Once the web server access logs have been processed using SAWMILL, a list of referer entries can be generated, which would appear as shown in the figure below (click to enlarge).
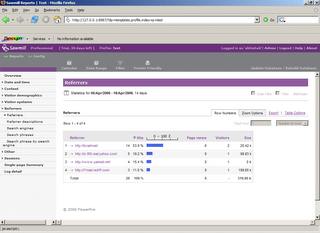
The ‘referers’ can then be analyzed for suspicious entries such as presence of IP address or organization name. See the previous post here to understand a suspicious referer. If a suspicious referer is found then that link can be followed and further analyzed. Of course to be effective in detecting a phishing attack the log analysis process has to be a regular activity.

0 Comments:
Post a Comment
<< Home